45 security labels access control
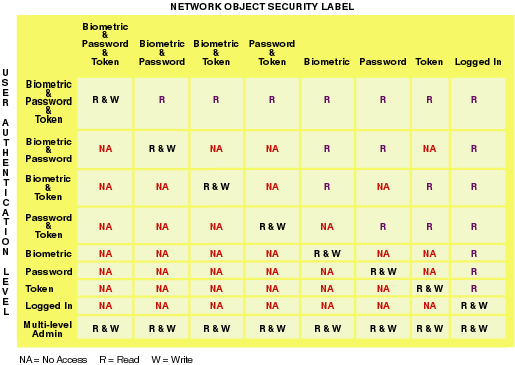
Conditional Access and Access Control – Azure AD | Microsoft ... This security policy enforcement engine analyzes real-time signals to make security enforcement decisions at critical checkpoints. The left side of the diagram represents how signals from users, devices, locations, apps, data labels, and risk analysis are aggregated; decisions are enforced based on the aggregated signals. Access Control Models – UHWO Cyber Security Dec 06, 2002 · It is not possible for users to change access control of a resource. MAC uses “security labels” to assign resource objects on a system. There are two pieces of information connected to these security labels: classification (high, medium, low) and category (specific department or project – provides “need to know”).
Comparing Access Control: RBAC, MAC, DAC, RuBAC, ABAC - TechGenix Mar 30, 2022 · Types of Access Control. Access control is one of the easiest and most effective ways to meet your security needs. Yet, not all techniques work the same way. In this section, I’ll go through the 5 main types of access control you’ll run into. 1. Mandatory Access Control (MAC) Above all others, MAC is the most strictly enforced control method.
Security labels access control
Access Control | OWASP Foundation Access Control, also known as Authorization — is mediating access to resources on the basis of identity and is generally policy-driven (although the policy may be implicit). It is the primary security service that concerns most software, with most of the other security services supporting it. Security - FHIR v4.3.0 - Health Level Seven International Two of the classic Access Control models are: Role-Based Access Control (RBAC), and Attribute-Based Access Control (ABAC). In Role-Based Access Control (RBAC), permissions are operations on an object that a user wishes to access. Permissions are grouped into roles. A role characterizes the functions a user can perform. Roles are assigned to users. Access control - Wikipedia The term access control refers to the practice of restricting entrance to a property, a building, or a room to authorized persons. Physical access control can be achieved by a human (a guard, bouncer, or receptionist), through mechanical means such as locks and keys, or through technological means such as access control systems like the mantrap ...
Security labels access control. Computer access control - Wikipedia In computer security, general access control includes identification, authorization, authentication, access approval, and audit.A more narrow definition of access control would cover only access approval, whereby the system makes a decision to grant or reject an access request from an already authenticated subject, based on what the subject is authorized to access. Access control - Wikipedia The term access control refers to the practice of restricting entrance to a property, a building, or a room to authorized persons. Physical access control can be achieved by a human (a guard, bouncer, or receptionist), through mechanical means such as locks and keys, or through technological means such as access control systems like the mantrap ... Security - FHIR v4.3.0 - Health Level Seven International Two of the classic Access Control models are: Role-Based Access Control (RBAC), and Attribute-Based Access Control (ABAC). In Role-Based Access Control (RBAC), permissions are operations on an object that a user wishes to access. Permissions are grouped into roles. A role characterizes the functions a user can perform. Roles are assigned to users. Access Control | OWASP Foundation Access Control, also known as Authorization — is mediating access to resources on the basis of identity and is generally policy-driven (although the policy may be implicit). It is the primary security service that concerns most software, with most of the other security services supporting it.












Post a Comment for "45 security labels access control"